You are here
On my Kindle I am root

Starting from the end
That's my Kindle in the screenshot running a full screen terminal. I'm about to run nmap (a network mapping program) inside a chrooted Debian ARM installation I put on the device. Having Debian on the device isn't really necessary for hacking the Kindle but it does make it easier to install ARM binaries of just about any of the 25,000 packages in Debian. Yep, apt-get works on my Kindle!
More practically I can now SSH into the device over the WIFI, use SFTP to transfer over new books without having to mess around with a USB cable, etc.
The device can still gets books from Amazon, but I've disabled its ability to auto-update firmware. Now that I control my device I'd like to keep it that way, even if there's no immediate practical benefit.
Besides, it's one thing to know on a theoretical level that the device runs Linux, and being able to see for yourself which processes are running:
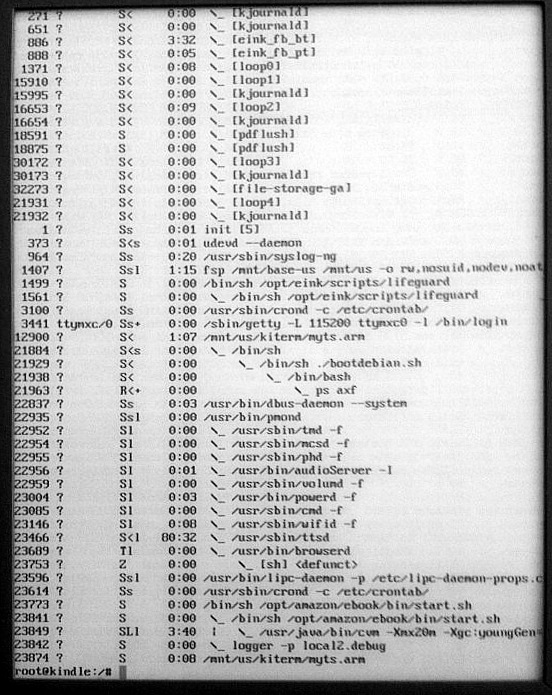
Rewinding back to the beginning
Besides my workstation, my Kindle is the device I use the most. By far.
So much that it's almost wearable computing by now. When I take a break I stick it in my pocket and have Tom Glynn's synthesized voice quickly humming whatever I'm reading to me while my hands are free to eat my meals, take care of boring errands, etc.
It's maybe the only mobile device I feel has unambiguously improved my quality of life in a net positive way (I'll leave my gripes with smart phones for another time).
My only major concern with the Kindle is that I'm not supposed to have full control over it:
-
If it's connected to a network, Amazon can update my firmware remotely at any time without asking me first, possibly changing the device's behavior in undesirable ways. They can spy on my reading (how would I know?), delete my books, etc.
-
I can't customize its behavior. I keep having these ideas on little features that would make the device even more useful to me but probably wouldn't make sense for the average user. I don't expect Amazon (or any other consumer company for that matter) to design a product that fits perfectly with my needs out of the box.
-
I know there's Linux under the hood and I want root on it. On principle dammit!
OK, maybe not just on principle. The Kindle is a very low cost, super lightweight, ARM Linux machine with an eInk display that can be easily read in bright sunlight, a great text-to-speech system, amazing battery life, WIFI / 3G access, a nice bit of storage, sound output and even a hidden microphone. There are endless creative off-label things you could do with it.
Considering all the features packed into the Kindle the price is jaw dropping. Amazon probably isn't making a profit on the hardware. Heck the "special offers" Kindle now costs just $79. That's $20 less the $99 ARM SheevaPlug which doesn't have nearly as many features.
So over the weekend I took a look and it turns out that since I last checked a nice Kindle hacking community has sprung up, discovered that the Kindle doesn't have any real security, and made available all the tools you need to take full control over your device.
Kindle hacking is at its infancy but there's already a pretty sweet list of homebrew hacks that let you for example, replace the dead people in your screensavers, change/add new fonts, etc.
I found everything online. Mostly on the excellent mobileread forums but it took time to make sense of it all. The documentation is often a somewhat confusing and dodgy patchwork so I took notes, tested what worked on my Kindle and figured it would be useful to summarize my "crystallized" understanding for the benefit of others who might want to go down the same road.
Rooting your Kindle
Under the hood Amazon's firmware updates are just glorified shell scripts in a proprietary package format that contains an embedded Amazon signature.
The first thing we need to do to get control of the device is "jailbreak" it, which really just adds a "hacked" key to the keyring used to verify the package signature.
Install the Jailbreak
http://wiki.mobileread.com/wiki/Kindle_Screen_Saver_Hack_for_all_2.x_and_3.x_Kindles
See the "How to install Jailbreak Hack" section.
Currently the latest version of the JailBreak is 0.7. To install it you just transfer over the bin that's right for your version of the Kindle (I.e., update_jailbreak_0.7.N_k3w_install.bin = Kindle 3 Wifi) into the device root and then update the device:
Home > Settings > Menu > Update Kindle
Now you can install packages signed by a non-secret hacked key. The Jailbreak contains a whitelist of md5sums of known good hacks.
Install usbnet hack
I downloaded the usbnet hack from an attachment on this forum thread:
http://www.mobileread.com/forums/showthread.php?t=88004
What's usbnet?
The Kindle 2 has a hidden USB network mode, probably left over from development. When activated, the Kindle would behave as a USB network device rather than a USB mass storage device. This allowed you to do neat things such as tethering the device to your laptop.
Kindle 3 seems to have removed this feature, but the usbnet hack reactivates it and installs busybox (a micro shell environment), dropbear (a micro SSH server) and a few other utilities to allow you to SSH into your device and explore its insides.
After installation, usbnet creates a usbnet directory in your kindle root which contains its configuration files:
$ cd /mnt/kindle/usbnet $ find ./info.txt ./DISABLED_auto ./run ./run/telnetd.pid ./run/sshd.pid ./etc ./etc/dropbear_rsa_host_key ./etc/htoprc ./etc/dropbear_dss_host_key ./etc/config ./etc/terminfo ./etc/terminfo/x ./etc/terminfo/x/xterm ./etc/authorized_keys ./etc/bak ./etc/bak/dropbear_dss_host_key ./etc/bak/dropbear_rsa_host_key ./bin ./bin/busybox ./bin/usbnet-enable ./bin/dropbearmulti ./bin/usbnet-disable ./bin/usbnetwork ./bin/rsync ./bin/sftp-server ./bin/lsof ./bin/htop ./usbnetwork_install.log
Now we'll unmount (I.e., "eject") the Kindle from our computer, disconnect the USB connection to take it out of mass storage mode and enable usbnet mode.
-
Press [DEL] on your Kindle to bring up the search bar and do the following "searches":
;debugOn ~help # just for fun ~usbNetwork ;debugOff
The commands are not case sensitive. Usually you don't want to stay in debugging mode because it turns off various power savings features such as turning off WIFI is your Kindle is not connected to the USB. Also, it turns on verbose logging.
Now when you connect your Kindle to your computer via USB, it isn't recognized as a mass storage device but rather as a USB network device.
This is what dmesg says when I connect the Kindle in mass storage mode:
[138591.847428] usb 8-1: new high speed USB device using ehci_hcd and address 45 [138592.000857] usb 8-1: configuration #1 chosen from 1 choice [138592.004480] scsi24 : SCSI emulation for USB Mass Storage devices [138592.004541] usb-storage: device found at 45 [138592.004556] usb-storage: waiting for device to settle before scanning [138596.996774] usb-storage: device scan complete [138596.997900] scsi 24:0:0:0: Direct-Access Kindle Internal Storage 0100 PQ: 0 ANSI: 2 [138597.003881] sd 24:0:0:0: [sdc] 6410688 512-byte hardware sectors (3282 MB) [138597.109966] sd 24:0:0:0: [sdc] Write Protect is off [138597.109973] sd 24:0:0:0: [sdc] Mode Sense: 0f 00 00 00 [138597.109976] sd 24:0:0:0: [sdc] Assuming drive cache: write through [138597.113952] sd 24:0:0:0: [sdc] 6410688 512-byte hardware sectors (3282 MB) [138597.219787] sd 24:0:0:0: [sdc] Write Protect is off [138597.219792] sd 24:0:0:0: [sdc] Mode Sense: 0f 00 00 00 [138597.219794] sd 24:0:0:0: [sdc] Assuming drive cache: write through [138597.219799] sdc: sdc1
And here's what dmesg says when I connect the Kindle in USB network mode:
[138741.453693] usb 8-1: new high speed USB device using ehci_hcd and address 48 [138741.604690] usb 8-1: configuration #1 chosen from 2 choices [138741.610967] usb0: register 'cdc_ether' at usb-0000:00:1d.7-1, CDC Ethernet Device, ee:49:00:00:00:00
Note that with the usbnet hack, by default SSH only works over the USB host-to-host connection. SSH is configured not to ask for the root password so usbnet wisely disables SSH over WIFI for security reasons.
To safely turn SSH over WIFI on we'll want to harden our Kindle first a bit. Setup SSH authentication, change the default keys and passwords and then reconfigure usbnet to allow SSH over WIFI.
We can configure this stuff in mass storage mode by editing files in usbnet/etc under the Kindle root, or via SSH on the usb host-to-host network. BTW, the kindle root you see in mass storage mode is is mounted to /mnt/us on the Kindle.
Anyhow, after connecting the Kindle to our computer in usbnet mode we have a new device, usb0 which we will configure to suit the default usbnet setup:
$ sudo ifconfig usb0 192.168.2.1 $ ping 192.168.2.2 PING 192.168.2.2 (192.168.2.2) 56(84) bytes of data. 64 bytes from 192.168.2.2: icmp_seq=1 ttl=64 time=0.696 ms --- 192.168.2.2 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 0.696/0.696/0.696/0.000 ms
Now let's login to our Kindle for the first time:
$ ssh 192.168.2.2
Welcome to Kindle!
#################################################
# N O T I C E * N O T I C E * N O T I C E #
#################################################
Rootfs is mounted read-only. Invoke mntroot rw to
switch back to a writable rootfs.
#################################################
[root@kindle root]# cat /proc/cpuinfo
Processor : ARMv6-compatible processor rev 3 (v6l)
BogoMIPS : 511.18
Features : swp half thumb fastmult vfp edsp java
CPU implementer : 0x41
CPU architecture: 6TEJ
CPU variant : 0x1
CPU part : 0xb36
CPU revision : 3
Cache type : write-back
Cache clean : cp15 c7 ops
Cache lockdown : format C
Cache format : Harvard
I size : 16384
I assoc : 4
I line length : 32
I sets : 128
D size : 16384
D assoc : 4
D line length : 32
D sets : 128
Hardware : Amazon MX35 Luigi Board
Revision : 35020
Serial : "B008A0A0040298FC"
BoardId : "SP1B000000000000"
[root@kindle root]# free
total used free shared buffers cached
Mem: 256536 151468 105068 0 15248 53372
-/+ buffers/cache: 82848 173688
Swap: 0 0 0
[root@kindle root]# mntroot rw
system: I mntroot:def:Making root filesystem writeable
[root@kindle root]# passwd root
Changing password for root
New password:
Retype password:
[root@kindle root]# cd /mnt/us
[root@kindle us]# ls
audible documents music system
usbnet linkjail
[root@kindle us]# cd usbnet/etc/
[root@kindle etc]# ls -l
-rwxr-xr-x 1 root root 957 May 23 14:56 config
-rwxr-xr-x 1 root root 458 May 23 01:54 dropbear_dss_host_key
-rwxr-xr-x 1 root root 427 May 23 01:54 dropbear_rsa_host_key
-rwxr-xr-x 1 root root 561 Oct 10 2010 htoprc
drwxr-xr-x 3 root root 8192 May 22 20:59 terminfo
# setup my SSH key as an authorized key
[root@kindle etc]# echo ssh-rsa AAAAB3NzaC1yc2EAAAABIwAwAIEAvp+4FpjKlv1nsddevQtX8zMvQMkuJDwZSCHpFdm2IY20NmOhF0LY6dKRzQ+89pJ2MUYZYtotN1SmMk1ndUmHssQIRrmKKWdwnDzDUISTDB5iEQIg8JcPxwu6+uJnLrZvfNrx/fsMoRwRR3S9bHcKi9pxQT9T4Jbt+Gt6ewtuLAE= liraz@dev > authorized_keys
Note that with the usbnet hack, by default SSH doesn't ask for the root password so it disables SSH over WIFI for security reasons.
In summary here's what I did to enable SSH over WIFI safely:
-
added my SSH key to usbnet/etc/authorized_keys (a new file).
-
installed dropbear on my Ubuntu workstation (e.g,. apt-get install dropbear) and then recreated the dropbear host keys:
dropbearkey -t rsa -f rsa dropbearkey -t dss -f dss scp rsa 192.168.2.2:/mnt/us/usbnet/etc/dropbear_rsa_host_key scp dss 192.168.2.2:/mnt/us/usbnet/etc/dropbear_dss_host_key
-
edit usbnet/etc/config to change K3_WIFI field from false to true
-
restart usbnet by toggling it off and back on with the hidden ~usbNetwork comand (from the search bar in ;debugOn mode).
Test that you can still log into SSH via the usb0 connection. That means you've configured everything correctly.
Now turn on Wifi and see if you can log in over WIFI. You can find out the Kindle's IP address by accessing the secret 711 network info screen:
Home > Menu > Settings >
# ALT + U Q Q
711
As long as your Kindle is plugged into USB (in your computer or the power charger), it will remain accessible via WIFI even if the screensaver is active. In debugging mode the WIFI stays on even when your Kindle is not plugged in.
As is typical for embedded ARM devices the WIFI chip is usually sleeping to conserve power which makes for a slightly jittery interactive SSH session. Not too bad though.
For extra convenience, I configured my local WIFI router to bind the Kindle always to the same IP address (e.g., 10.0.0.15).
Keep in mind that your Kindle filters out ICMP pings on the WIFI so it won't respond to a regular ping, but it will respond to arping:
$ sudo arping 10.0.0.15
ARPING 10.0.0.15
42 bytes from ee:19:00:00:00:00 (10.0.0.15): index=0 time=1.777 msec
42 bytes from ee:19:00:00:00:00 (10.0.0.15): index=1 time=54.230 msec
$ nc -vv 10.0.0.15 22
10.0.0.15 22 (ssh) open
SSH-2.0-dropbear_0.53.1
$ ssh 10.0.0.15
Welcome to Kindle!
#################################################
# N O T I C E * N O T I C E * N O T I C E #
#################################################
Rootfs is mounted read-only. Invoke mntroot rw to
switch back to a writable rootfs.
#################################################
[root@kindle root]# ifconfig
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:25 errors:0 dropped:0 overruns:0 frame:0
TX packets:25 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2496 (2.4 KiB) TX bytes:2496 (2.4 KiB)
usb0 Link encap:Ethernet HWaddr EE:19:00:00:00:00
inet addr:192.168.2.2 Bcast:192.168.2.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:647 errors:0 dropped:0 overruns:0 frame:0
TX packets:428 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:53670 (52.4 KiB) TX bytes:56067 (54.7 KiB)
wlan0 Link encap:Ethernet HWaddr 28:EF:01:83:A1:2C
inet addr:10.0.0.15 Bcast:10.0.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3079 errors:0 dropped:0 overruns:0 frame:0
TX packets:727 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:333515 (325.6 KiB) TX bytes:57404 (56.0 KiB)
[root@kindle root]# netstat -atn
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:8784 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:8022 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:40317 0.0.0.0:* LISTEN
tcp 0 0 10.0.0.15:22 10.0.0.10:41208 ESTABLISHED
tcp 0 496 10.0.0.15:22 10.0.0.10:41209 ESTABLISHED
tcp 0 0 192.168.2.2:22 192.168.2.1:48703 ESTABLISHED
[root@kindle root]# iptables --list
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpt:40317
ACCEPT tcp -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT tcp -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT udp -- anywhere anywhere state ESTABLISHED
ACCEPT udp -- anywhere anywhere state ESTABLISHED
ACCEPT all -- localhost.localdomain anywhere
ACCEPT all -- anywhere anywhere
ACCEPT icmp -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT tcp -- anywhere anywhere tcp dpt:ssh
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere localhost.localdomain
I transfered over a 50MB test file to test the transfer rate. With good connectivity I can get 1.5MB/s over the Wifi. The USB host-to-host is slightly faster at about 2MB/s, and the mass storage interface is fastest at 6MB/s.
Transfering Kindle ebooks over Wifi with SSH/SFTP
Example:
scp path/to/ebook.prc 10.0.0.15:/mnt/us/documents ssh 10.0.0.15 dbus-send --system /default com.lab126.powerd.resuming int32:1
That last command triggers Amazon to refresh the book list. After I got sick of cut and pasting it into the CLI I made it into a tiny script:
cat > /usr/local/bin/hack-refresh << EOF #!/bin/sh dbus-send --system /default com.lab126.powerd.resuming int32:1 EOF chmod +x /usr/local/bin/hack-refresh
Note that in addition to its native AZW format, Amazon also supports txt, mobi, prc, mp3 and PDF files.
Unfortunately, the Kindle doesn't support local HTML files natively but there's a really sweet open source project called calibre for converting between ebooks formats.
Before Calibre, I also had some success with mobi pocket creator, a free as in beer program I experimented with in my Windows XP VM.
Install a native terminal (kiterm)
Luigi Rizzo wrote a standalone Kindle terminal you can use from within the device. I used a slightly patched version that works full screen.
It hasn't been packaged into a Kindle *.bin file yet but installation was relatively straightforward thanks to a nice tutorial on TinyApps.
The short version:
-
extract the zip file to /mnt/us/kiterm
-
create an init script to launch it on startup:
cat>/etc/init.d/kiterm<<'EOF' #! /bin/sh # /etc/init.d/kiterm case "$1" in start) echo "Starting kiterm " /mnt/us/kiterm/myts.arm & ;; stop) echo "Stopping kiterm " killall myts.arm ;; *) echo "Usage: /etc/init.d/kiterm {start|stop}" exit 1 ;; esac exit 0 EOF ln -s /etc/init.d/kiterm /etc/rc5.d/S97kiterm -
reboot the Kindle (Menu > Settings > Menu > Restart)
To access the Terminal you press Shift, let go and immediately press T.
The terminal configures various key bindings to make up for the all the missing keys missing from the Kindle's limited keyboard. I saved the most common ones to a text file on my kindle for reference:
[root@kindle root]# mntroot rw
system: I mntroot:def:Making root filesystem writeable
[root@kindle root]# cat>keys<<'EOF'
> Ctrl = AA (aka Symbol)
> Esc = Left Next Page
>
> .------------------------. .----------------------.
> | Key Back Back+Shift | | Key Alt Alt+Shift |
> +------------------------+ +----------------------+
> | Q ` ~ | | Q 1 ! |
> | A Tab Back Tab | | W 2 @ |
> | Z < > | | E 3 # |
> | U - _ | | R 4 $ |
> | I = + | | T 5 % |
> | O [ { | | Y 6 ^ |
> | P ] } | | U 7 & |
> | K ; : | | I 8 * |
> | L ' " | | O 9 ( |
> | Del \ | | | P 0 ) |
> | . , < | '----------------------'
> | Sym . > |
> | Ret / ? |
> '------------------------'
> EOF
[root@kindle root]# mntroot ro
system: I mntroot:def:Making root filesystem read-only
Preventing Amazon from auto-updating your firmware
As far as I can tell the easiest and surest way to prevent Amazon from auto-updating your Kindle is to knock out the keys it uses to verify the signatures:
mv /etc/uks /etc/uks.disabled
Under the hood, the Kindle is programmed to get firmware updates automatically via the TODO service, which gives the Kindle a list of things to do including getting new books (or deleting existing books) and/or getting new firmware.
Some people in the community have gone as far as to change the URLs in the framework and pass them through a proxy server setup to selectively mirror Amazon's TODO requests.
# grep http /opt/amazon/ebook/config/framework.fiona.conf BASE_WEBSITE_URL: http://www.amazon.com CERT_SERVER_URL : https://fras-g7g.amazon.com/FrasProxy/ REGISTER_SERVER_URL : https://firs-g7g.amazon.com/FirsProxy/ TODO_SERVER=https://todo-g7g.amazon.com/FionaTodoListProxy/ CDE_SERVER=https://cde-g7g.amazon.com/FionaCDEServiceEngine/
Uninstalling hacks
All the hacks I've come across so far come with an installer and uninstaller *.bin files. Just in case, I copy the uninstaller for the hacks I install to my Kindle's root under "uninstallers". That way I can always roll back hacks later if I want:
[root@kindle uninstallers]# cd /mnt/us/uninstallers [root@kindle uninstallers]# ls update_jailbreak_0.7.N_k3w_uninstall.bin update_usbnetwork_0.33.N_k3w_uninstall.bin
Further reading
Stuff I still haven't figured out
- How do I speed up the text-to-speech? Even at Amazon's fastest default rate the Kidnle's TTS voice isn't speaking as fast as I can read with my eyes. Make it gI want it to go faster!
- How do I replace the TTS voice? I'm hoping the Polish hacker that got his Kindle to speak in Polish will share more details on his brilliant hack
- How do I map all the dbus targets on the Kindle? I bet that would be useful in scripting the Kindle to new things.
Comments
I wonder how that happened...
Wow this sounds so awesome Liraz
I want to root my Kindle now too! :) Although I must admit that I get a little nervious about hacking devices. I think of all the silly things I've done on PCs over the years and the times I've foobarred OSs of all varieties with a few simple keystrokes... On a PC though clean install is (relatively) easy. Not always quite the case on a bricked device...
I appreciate the clear write up and I may well give this a go sometime soon! I'll post back if/when I do.
There doesn't seem to be a big risk of bricking the Kindle...
Once you get root, just try to avoid the urge to run this command:
Cool, thanks for the reassurance Liraz
Yeah I must admit it sounds pretty straight forward. And I have come a long way since my days of trashing stuff (it hasn't happened for a while now). And I think I can contain myself and hold back on deleteing the root fs! :)
It kind of makes me nervous though...
Ah, maybe that's just my inner security consultant coming out for air. Shoo!
Great breadcrumbing skills here. Thorough and interesting!
Maybe a memory stick upload to a Kindle, Android, Nook, what have you, would be an interesting take on a TKL setup. What stands out to me are the layers of modifications that it takes to get this to work together... and that you can piece the sequencing together.
Thinking about general Linux/Ubuntu/Debian how would one start to learn and understand the "startup roll" that one sees at boot time? Particularly, how to understand each of the components at loadup are referenced and where they each start and finish? I can chunder around a running system and get it to shutdown etc, but I would love to start to understand the configuration process in the context of the old "autoexec.bat" file.
Thanks for the good read Liraz!
Ubuntu and Debian use a different init / boot process
On Ubuntu they've introduced a replacement for SysV init called upstart to allow the system to boot up asynchronously. One of the things that means is that configuration tasks that can run in parallel do, and the initialization process only blocks for dependencies (e.g., network filesystems can't mount before the network comes up). Due to its parallel nature, exactly what happens in what order when your system boots up under Upstart is a bit hard to understand and predict, but many scripts, especially the server stuff still run in SysV init compatibility mode. Upstart scripts are in /etc/init.
Once you have the hacked
Once you have the hacked terminal service running: Shift. Let go. T.
Whist there is Kindle with keyboard
I wouldn't recommend it for any serious typing... I imagine that you are hoping to connect a 'proper' keyboard. TBH I am not sure if the hardware actually supports this, although it would be quite easy to test if you get a microUSB B (male - to connect to Kindle) to USB A (female - to connect to keyboard) adaptor then connect a USB keyboard to it and see what happens (note I imagine that you would have to root the Kindle first).
None of this will be much help though if you don't already have a Kindle. Unless you have one already, or want one anyway, I wouldn't buy one on the off chance that it will work...
IMO you'd be better off buying a cheap Android tablet. In my experience you should be able to do that no worries.
Pages
Add new comment